Security as a Service:
ConnX AI Secure Protection at the Perimeter and More.
ConnX Security as a Service
Simplify management, reduce expense, and ensure consistency and compliance
ConnX SECaaS offers a blended approach to data and voice security, ranging from stateful inspection, protocol anomaly detection, and intrusion prevention, to sophisticated application and user-aware learning and correlation techniques to provide a comprehensive security solution.
With today’s constant barrage of cyber threats and attacks, businesses are in a constant struggle to keep up and safeguard and protect itself. Many are turning to MSSPs (Managed Security Services Providers) to help protect their networks cost-effectively and reliably. But choosing an MSSP requires thought and research.
Not all offer the same levels of protection. You should focus your search on a provider with a solid track record and reputation.
ConnX Unified Security Management (USM), powered by AT&T Cybersecurity, simplifies operations, and ConnX Unified Communications Threat Management (UCTM), powered by Red Shift, is a subset specialized for voice.

Long gone are the ‘EYES ON GLASS’ days for monitoring and detection of threats and incidents.
With today’s elevated threat levels, you can’t take your eyes off the ball. That’s why you need a MSSP that takes a holistic approach, preferably by implementing a Security Information and Event Management (SIEM) solution. SIEM provides virtually complete visibility into your environment.
- Wholistic SIEM Solution
- 24/7 SOC Monitoring
- 24/7 Incident Response
- Integrated Threat Intelligence
- Vulnerability Assessment
ADVANTAGES

- Fast deployment
- Interoperability &
Integration
- Incident Report &
support
- Compliance Reports
- Asset Discovery
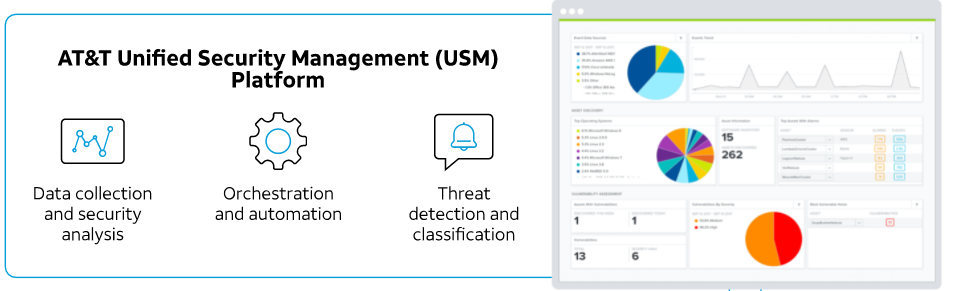
ConnX Unified Security Management

CONNX – AI SECURE USM PLATFORM
Powered by AT&T Cybersecurity
USM helps protect your assets deployed on-premises
and across both your public and private cloud environments through seven essential security capabilities in a single product:
- Asset Discovery – Know who and what is always connected to your environment
- Vulnerability Assessment – Know where vulnerabilities are on your assets to avoid compromise
- Intrusion Detection – Know when suspicious activities happen in your environment
- Endpoint Detection and Response – Continuously monitor your endpoints in the cloud and on premises to detect threats and changes to critical files
- Behavioral Monitoring – Identify suspicious behavior and potentially compromised systems
- SIEM Log Management – Correlate and analyze security event data from across your network and respond
- Security and Compliance Reporting – Pre-built, customizable reports for regulation standards and compliance framework
ConnX Security as a Service
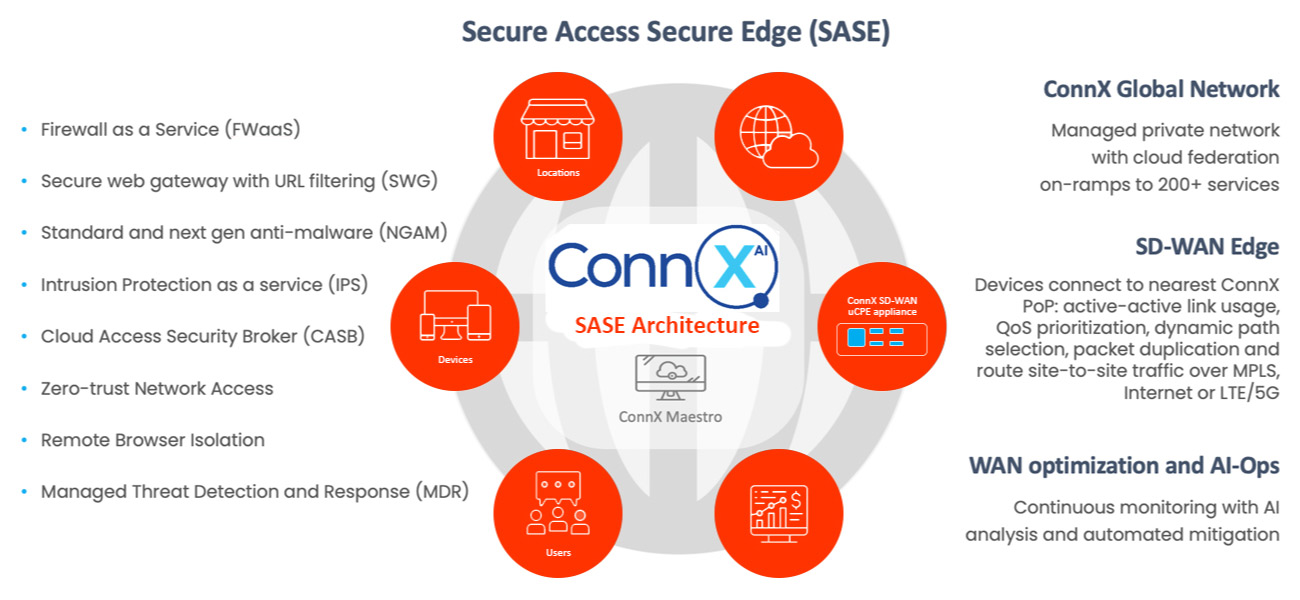
Secure Access Secure Edge (SASE) as a service architecture
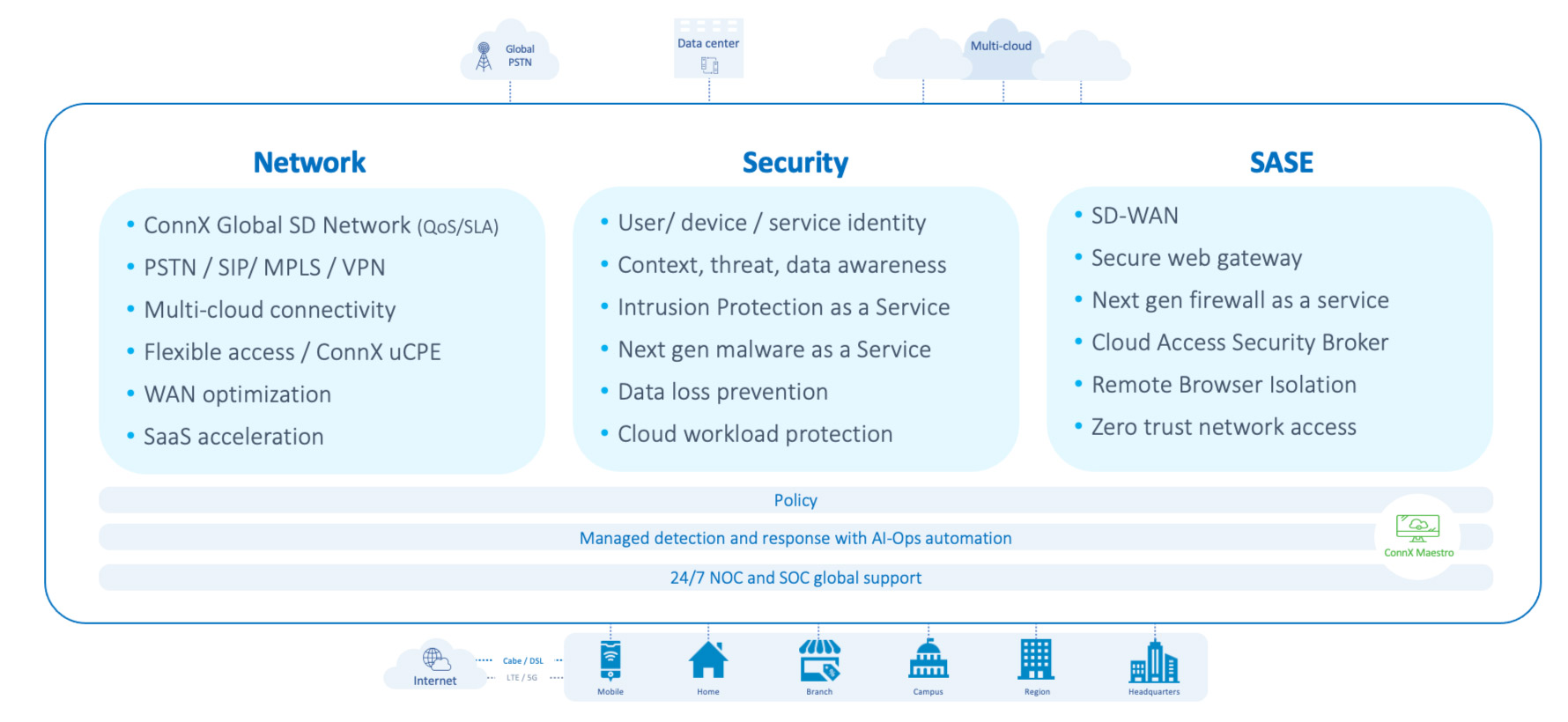
Integration with Other Managed Services Delivers Even More Value
ConnX AI Secure USM, powered by AT&T Cybersecurity
ConnX’s new SaaS integration with CONNX AI SECURE Networks UCTM allows enterprise operations and security teams to proactively detect threats, introduce real-time detection, and implement deep network analytics and security.
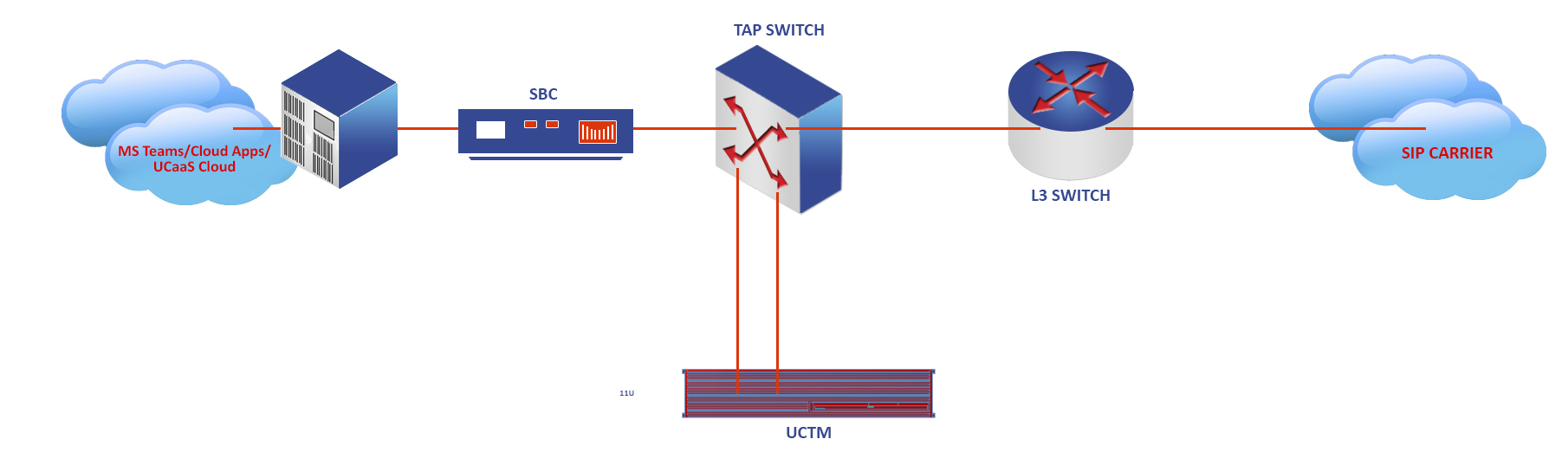
The CONNX AI SECURE Networks enterprise solution has the potential to resolve the most difficult threats including:
- As businesses turn to a global remote workforce, APTs are increasingly deployed as registration and Robocall flood attacks.
- Robocalls, APTs and UC spam attacks are easily detected and blocked.
- CONNX AI SECURE Networks Robocalls solution, which includes a multi sourced database of more than 3 million identified bad Robocalls numbers, increasing by 30,000 every day.
- The Advance Fraud Interdiction (AFI) role of CONNX AI SECURE Networks provides additional protection for blocking Robocalls and auto mitigation in real time
24/7 Global Security Threat Mapping
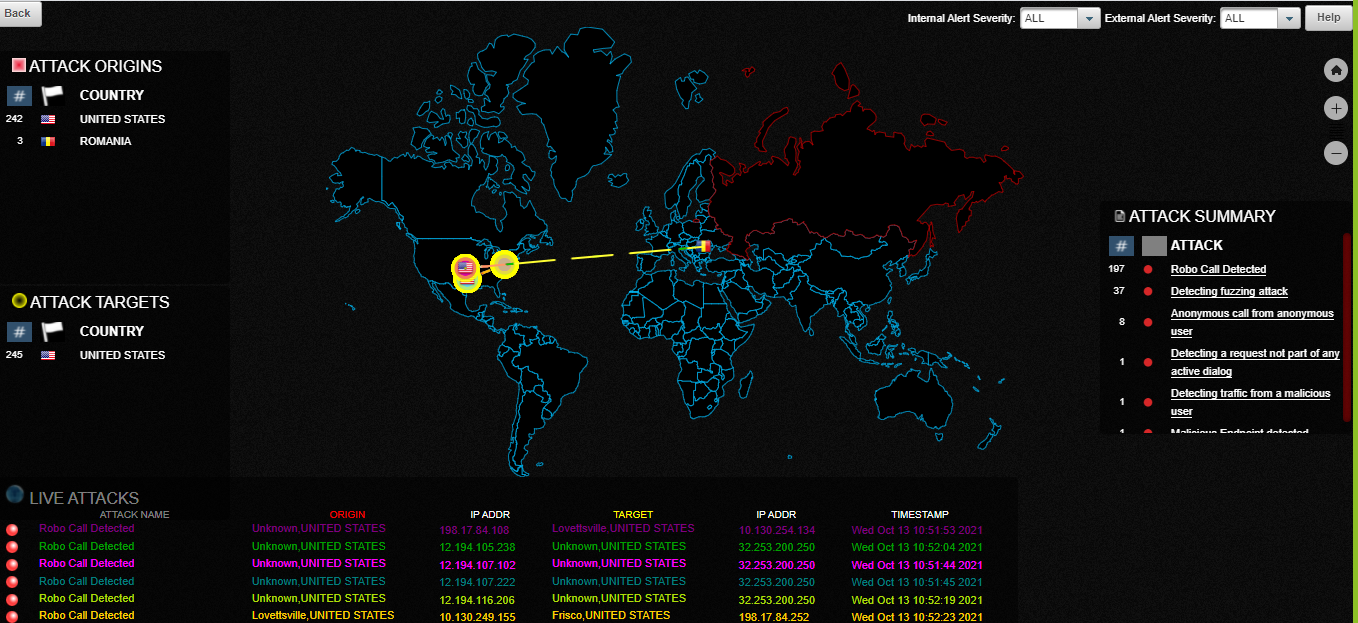
Fast Analysis, Actionable Results and
Intelligent Reporting
Uniquely Enabled by ConnX UCTM and powered by Redshift.
Challenges ConnX UTCM Addresses
Real-time security attacks
- T-DoS, Botnet & Zero-day attacks
- Robocalls & harassing callers
- Stealth – low volume attacks
Real-time fraud attacks
- Toll Fraud & call pumping
- Subscriber fraud, PBX hacking
- SPAM & nuisance calls
- Call spoofing & impersonation
SIP vulnerabilities (over 40,000 different VoIP threats and Attacks)
Source: Dark Reading 2020
Risks Mitigated
- Availability of network & UC service
- Confidentiality
- Financial consequences
- Identity theft
- IT systems attack through voice infrastructure
Save money, improve efficiencies, protect your infrastructure from the latest security threats, and strengthen your defenses while protecting your brand, and improving your bottom line.
Contact us for a free next-generation network, data, and application security assessment and learn more about the benefits of migrating to an AI-driven, cloud-based Security as a Service solution which includes unified voice, video, messaging, collaboration and contact center data protection.
